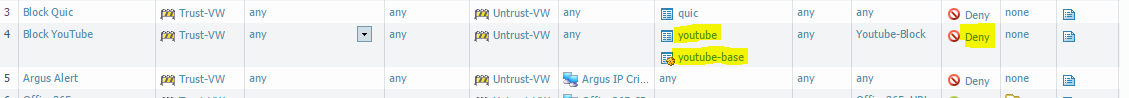
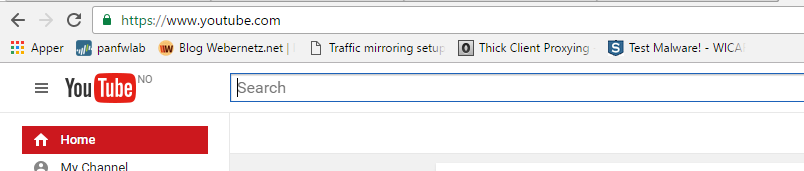
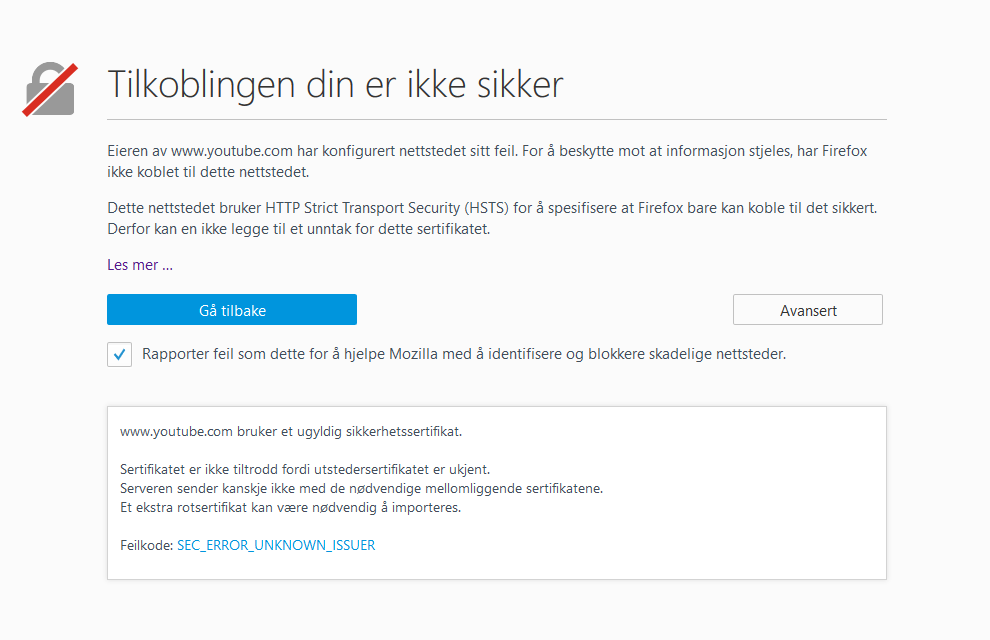
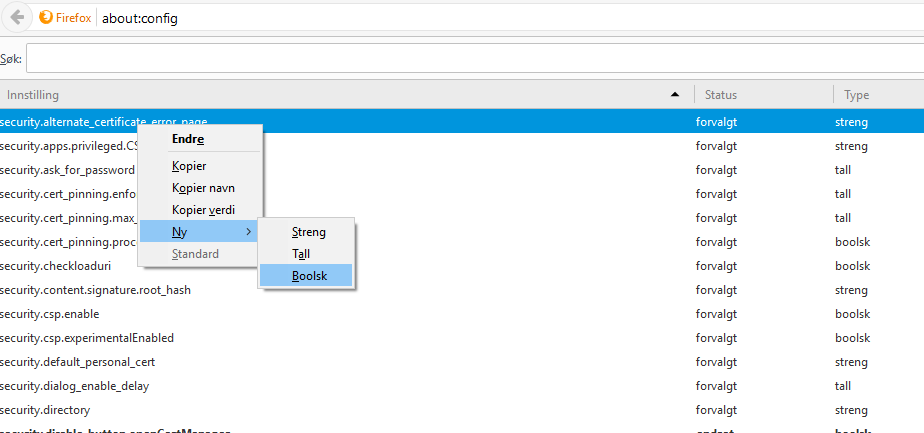
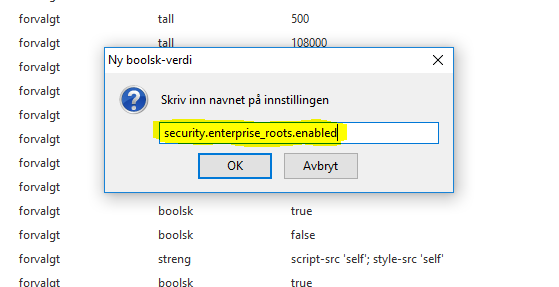
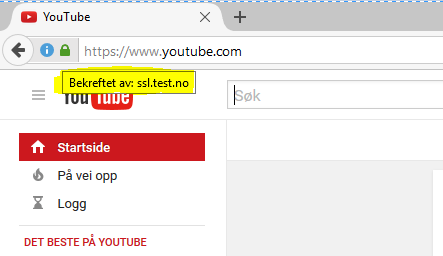
Let’s say you want to block YouTube, and you started making a rule, it would probably look something like this:
Block Youtube and Youtube-base and set it to deny, but this will not work if you are not running SSL-decryption:
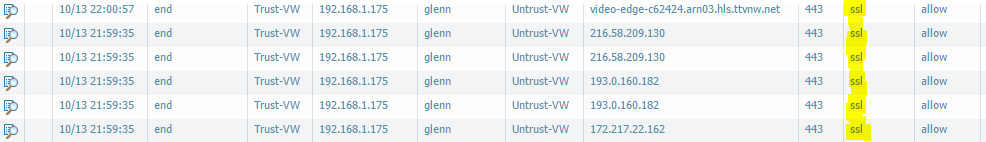
The application signatures is not able to identify the traffic correctly, since it’s inside an ssl-tunnel, and in the logs we can see this instead:
This gives us little to no information, so we need another way to do it..
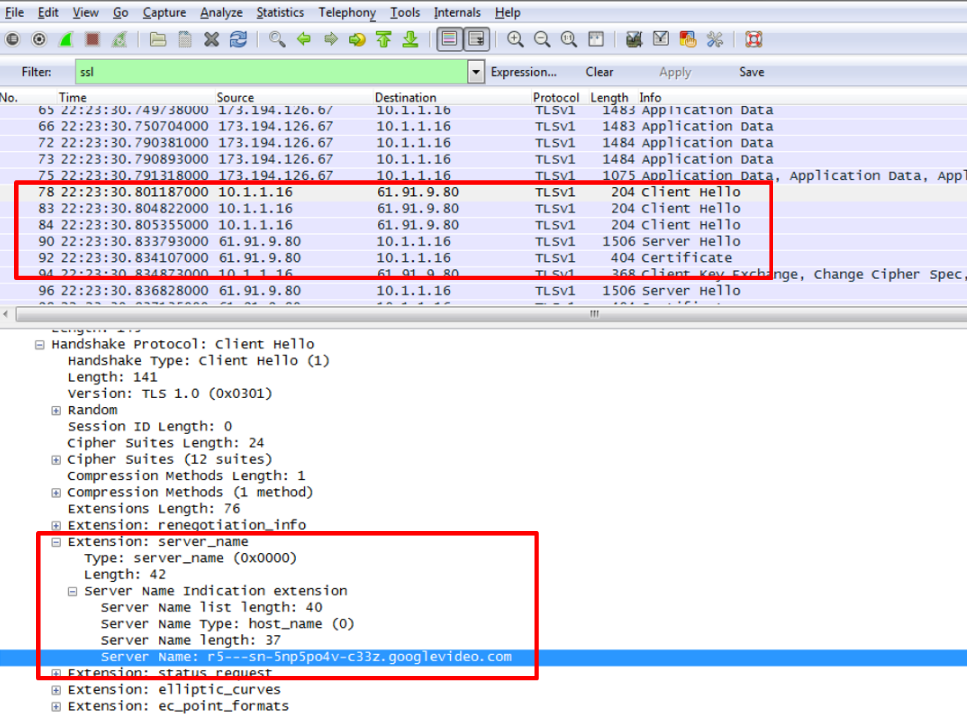
First some recon on the traffic:
This gives us some context we can work with, that are not encrypted.
So what do we do with it?
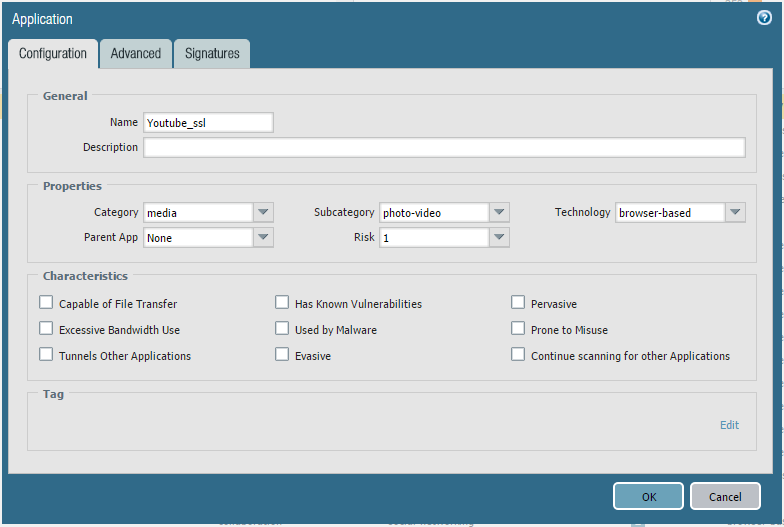
First we need to create a new custom application:
Objects -> Applications -> Add
Put in some information on what the application is doing and what the characteristics are, don’t just throw this together because it can end up matching an Application filter you don’t want it to match. Mine is a good example to start out with.
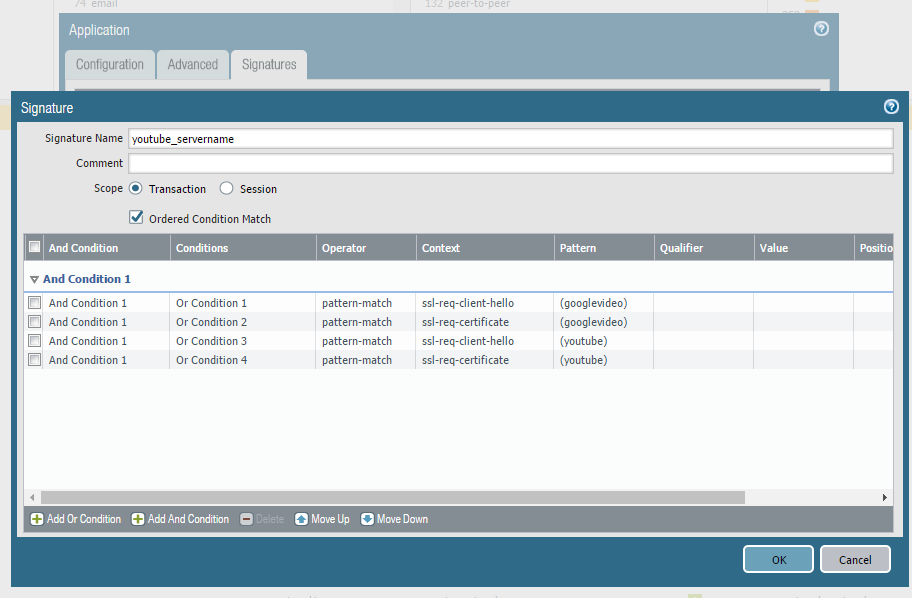
Next step is to add a new signature to actually identify Youtube traffic, and then add the conditions, so it matches the picture.
The signature is based on identifying the word youtube and googlevideo in both the SSL Client Hello and in the Certificate, this makes it possible for us to find and stop traffic to and from servers affiliated with Youtube.
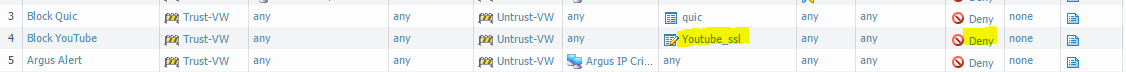
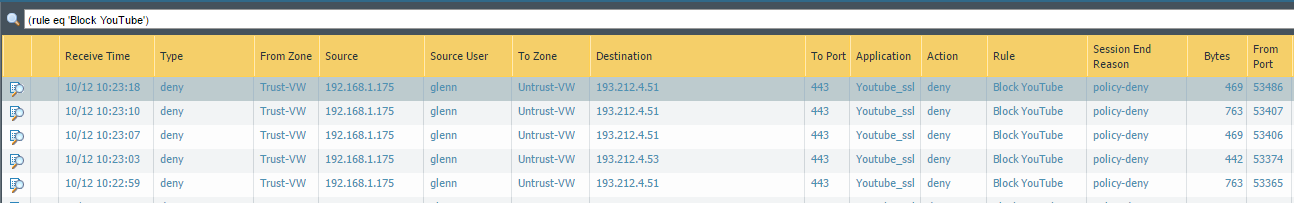
We then changes the application in our “Block Youtube” rule, and see what happens..
Chrome:
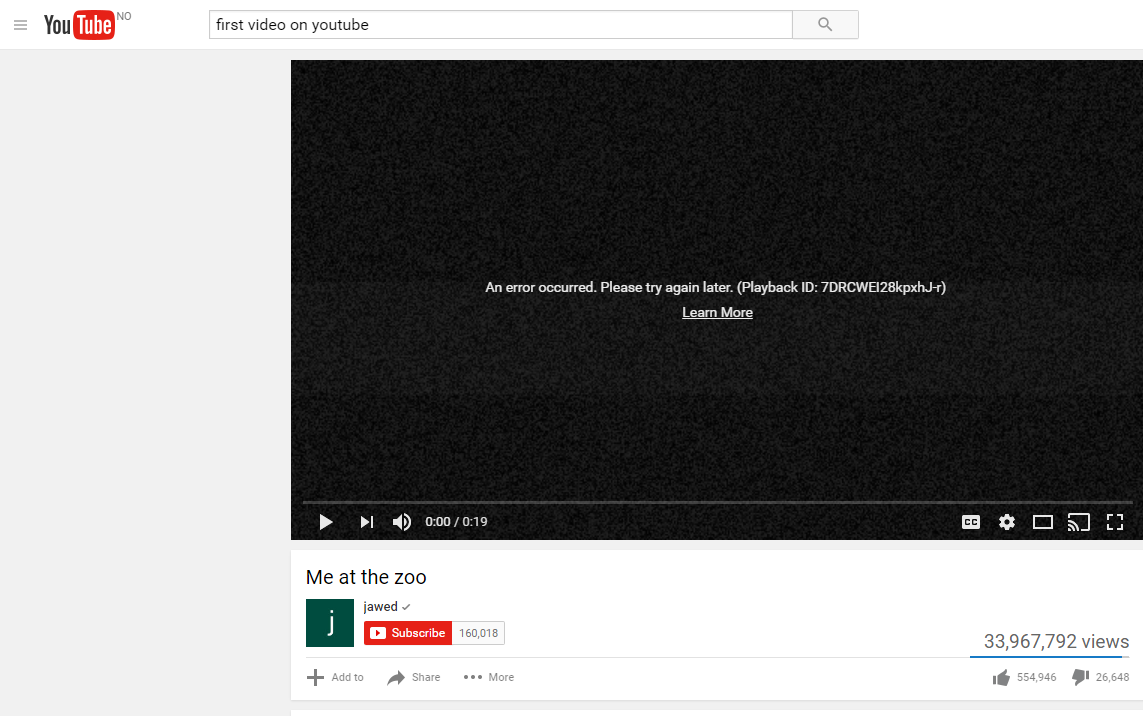
We still get into Youtube, due to how Chrome works, but we are able to block the videos.
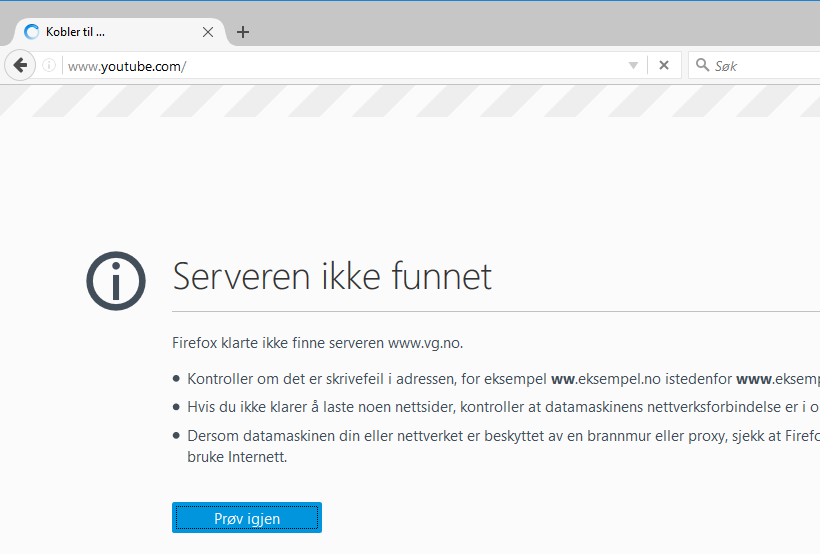
Firefox:
Totally blocked.
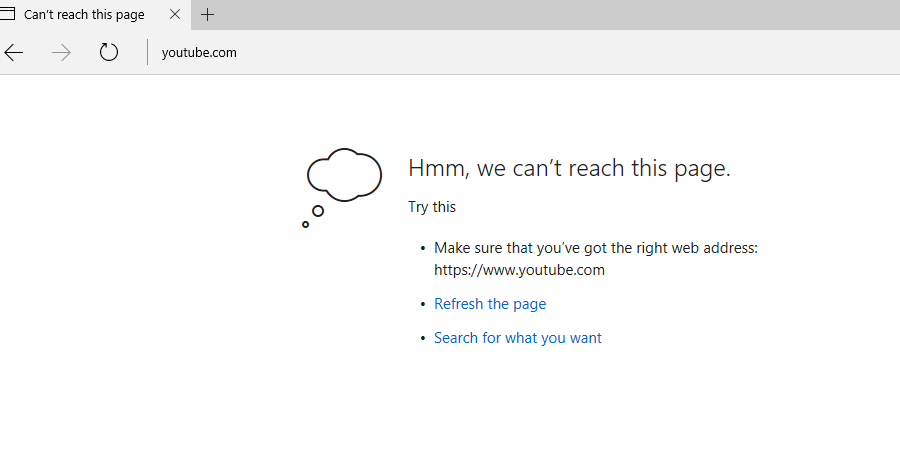
Internet Explorer:
So, we are able to block it, and we can see the result in the logs:
Link to my custom App-ID: appid_youtube_ssl
Disclaimer:
I don’t take any responsibility if this custom application breaks anything else except youtube. The signature is based on names in the certificate and client hello, so if you have other services using googlevideo or youtube, then they will also be blocked.