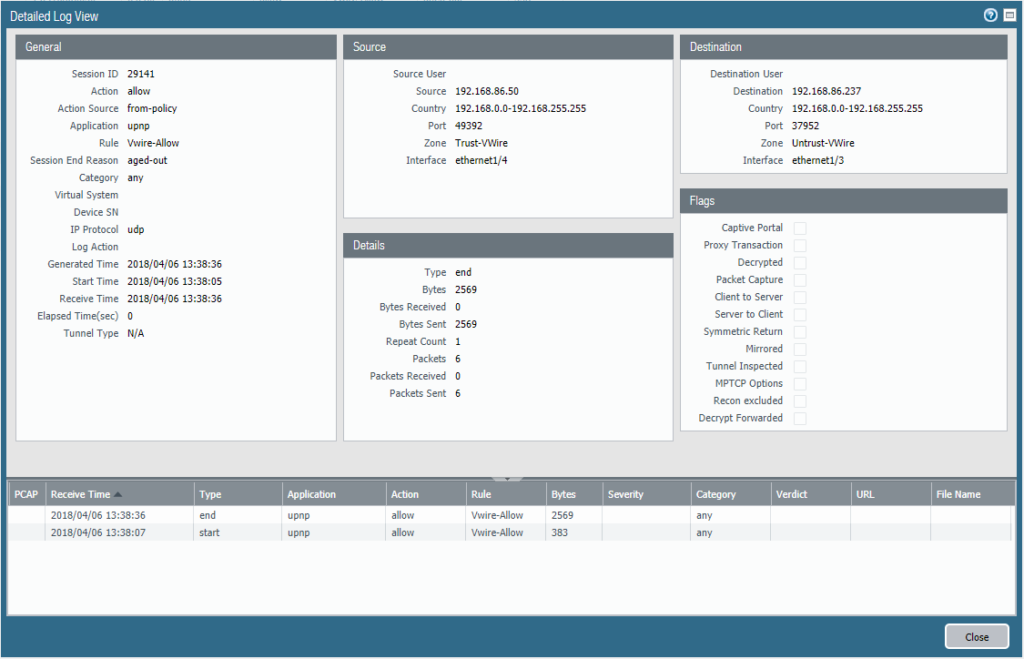
If you work with Palo Alto Networks firewalls, then this view is not new to you.
If not, then this is how the Detailed Log View from a standard Traffic log-line looks like. It contains a lot of information and helps you to figure out what has or has not happened.
But how many times have you not copy & pasted IPs, Domain-names or Threat-names/IDs to get more information from external sources?
For me, it’s plenty of times.
So let’s explore a cool feature of PanOS that has been around since the early beginning, and is not getting the recognition it should!
It’s simply called Log-links and is a feature where you can embed links directly into the Detailed Log View to attain information fast from external sources.
Here are the log-links I am showcasing today:
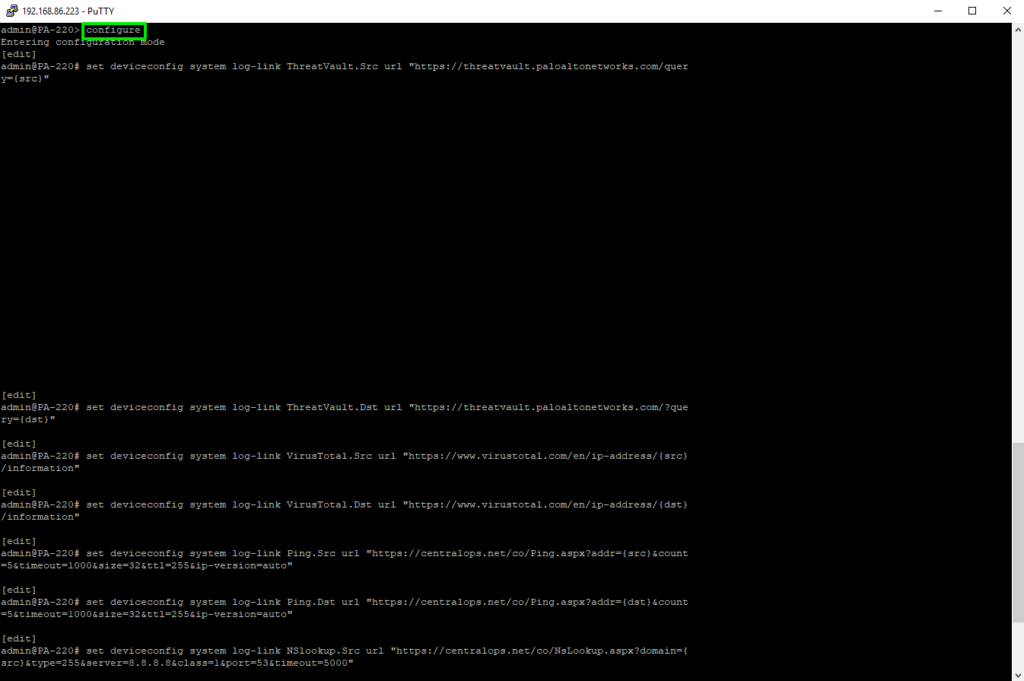
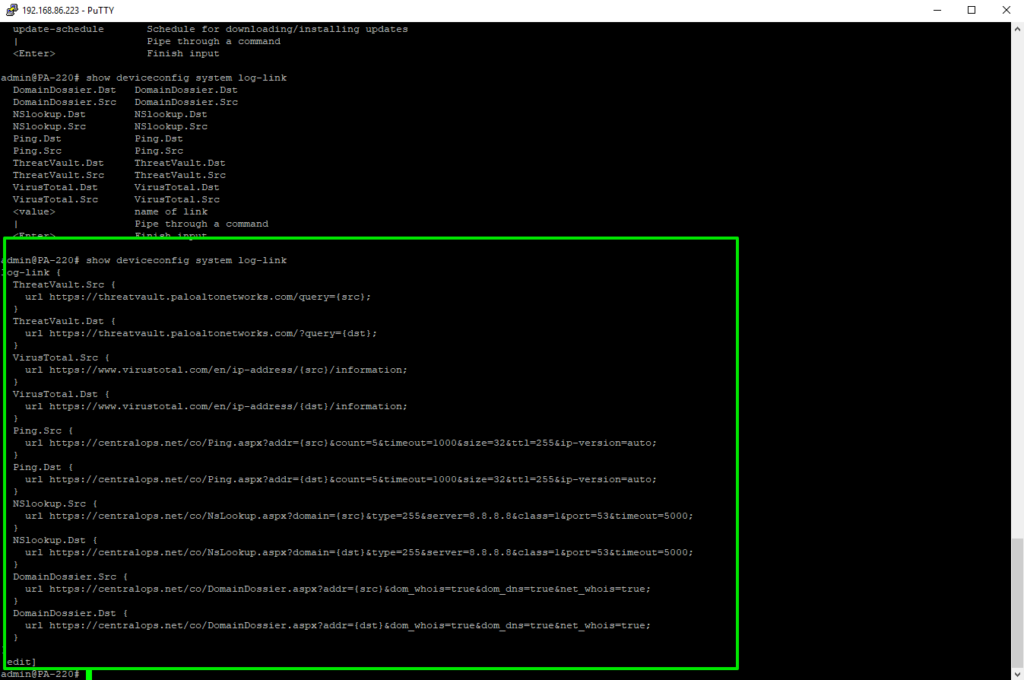
set deviceconfig system log-link ThreatVault.Src url "https://threatvault.paloaltonetworks.com/?query={src}"
set deviceconfig system log-link ThreatVault.Dst url "https://threatvault.paloaltonetworks.com/?query={dst}"
set deviceconfig system log-link VirusTotal.Src url "https://www.virustotal.com/en/ip-address/{src}/information"
set deviceconfig system log-link VirusTotal.Dst url "https://www.virustotal.com/en/ip-address/{dst}/information"
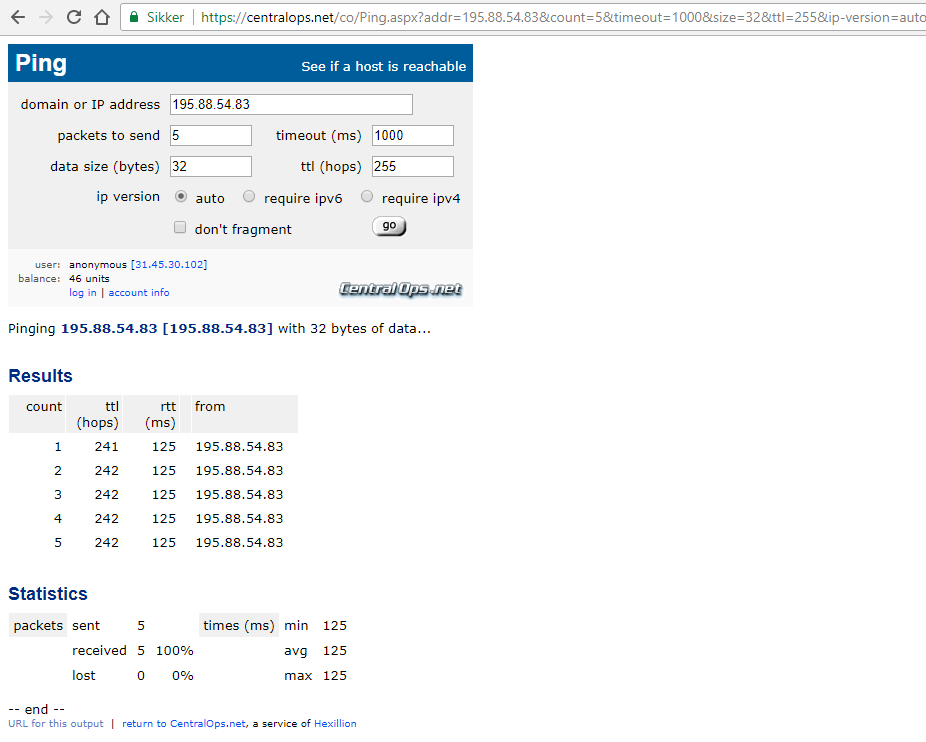
set deviceconfig system log-link Ping.Src url "https://centralops.net/co/Ping.aspx?addr={src}&count=5&timeout=1000&size=32&ttl=255&ip-version=auto"
set deviceconfig system log-link Ping.Dst url "https://centralops.net/co/Ping.aspx?addr={dst}&count=5&timeout=1000&size=32&ttl=255&ip-version=auto"
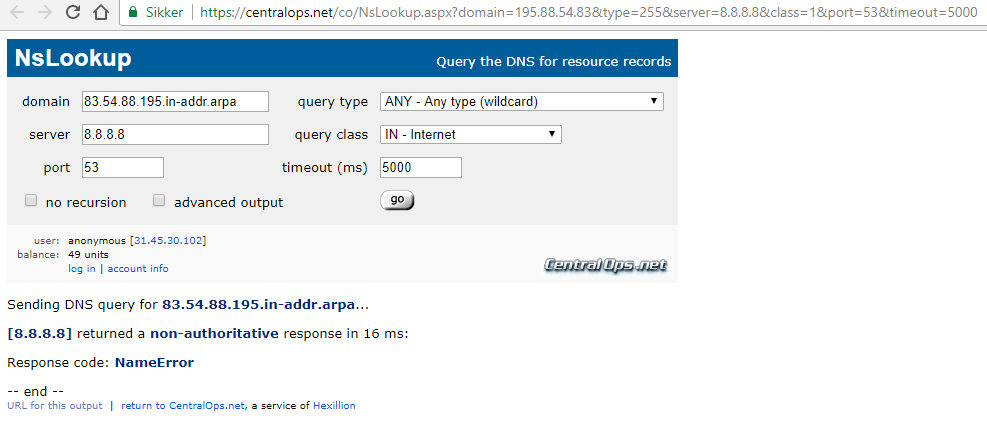
set deviceconfig system log-link NSlookup.Src url "https://centralops.net/co/NsLookup.aspx?domain={src}&type=255&server=8.8.8.8&class=1&port=53&timeout=5000"
set deviceconfig system log-link NSlookup.Dst url "https://centralops.net/co/NsLookup.aspx?domain={dst}&type=255&server=8.8.8.8&class=1&port=53&timeout=5000"
set deviceconfig system log-link DomainDossier.Src url "https://centralops.net/co/DomainDossier.aspx?addr={src}&dom_whois=true&dom_dns=true&net_whois=true"
set deviceconfig system log-link DomainDossier.Dst url "https://centralops.net/co/DomainDossier.aspx?addr={dst}&dom_whois=true&dom_dns=true&net_whois=true"
This is just example log-links, and as you can see from the formatting, it’s easy to implement other sites as well. The {src} and {dst} are just pointers to the Source and Destination address in the Logs.
You need to use CLI to get this to work, so simply fire up Putty or any other SSH tool to get started:
Remember that you need to be in “configure” mode to do this. Then simply copy-paste the above paragraph and commit after it is done.
NB: The links show from first to last, so try to add log-links for the same site right after each other to avoid it looking really messy.
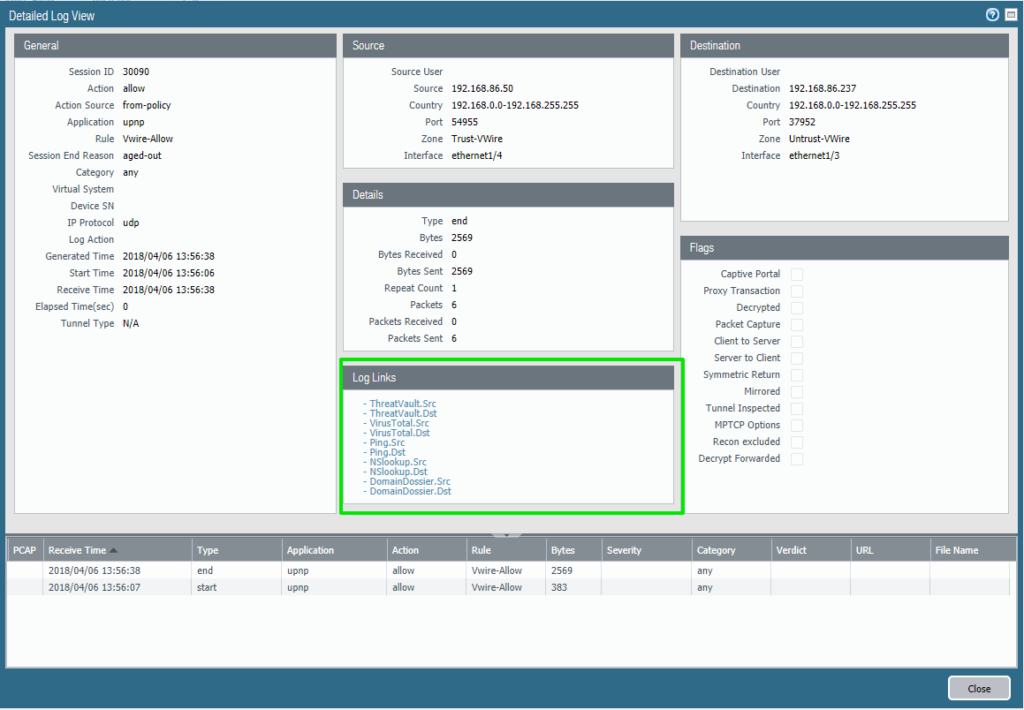
After it’s done committing you should see the following in the Detailed Log view(Remember to do a complete refresh of the GUI first.):
You have now a set of handy tools to check the IPs against Palo Alto Networks Threat Vault, VirusTotal, Ping from external destination, NSlookup from external source and Domain information.
When you press a link it will open a new window.
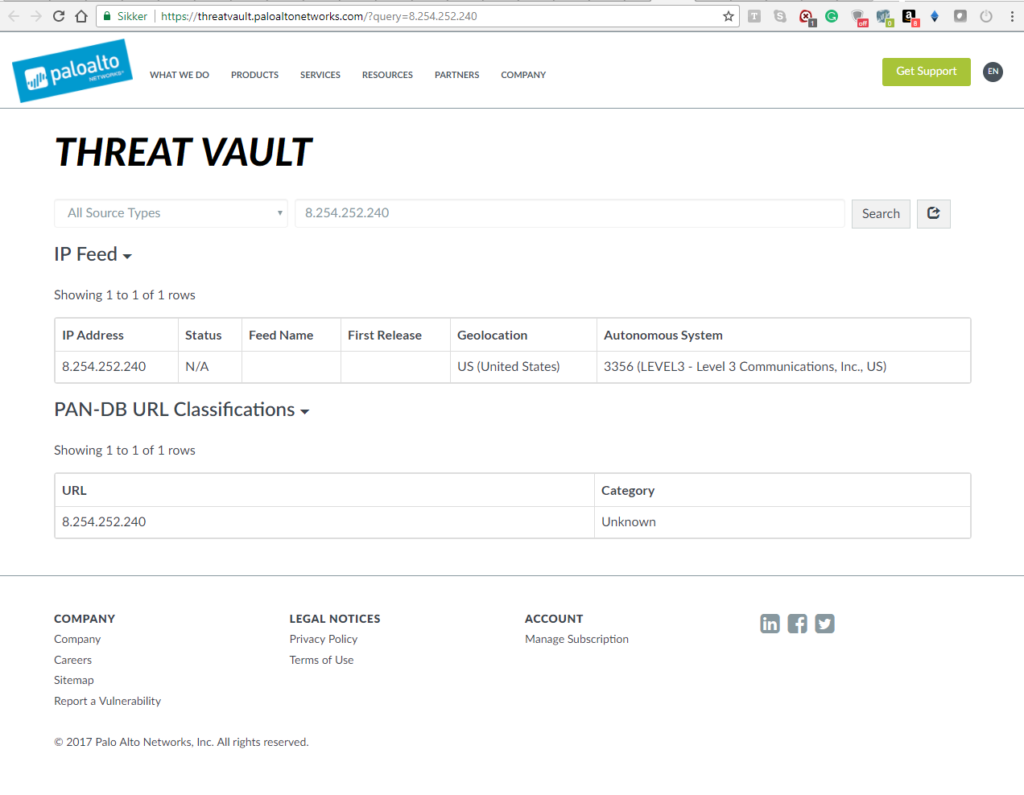
Here is a couple of expamples on how it looks:
And this is how it looks in CLI afterward:
It’s only your imagination that sets the limit on this feature, maybe you have internal tools as well you can now leverage directly into the log-links?
Have fun with it.
EDIT: Was a small typo in the first log-link.. this is now fixed. Sorry for everyone that was affected! 🙂