I have worked with SSL-decryption for several years, and one of my biggest issues during that time was the abundance of browsers that people use.
We have IE, Chrome, Firefox, Safari, Opera and many more, and they all have their own ideas on how things should work.
But the biggest issue I had was Firefox.
All the other browsers uses the built in certificate stores of both Mac OS X and Windows, this made it trivial to push out Certificates that would be used for SSL-decryption via GPO.
But not Firefox, they uses their own internal certificate store, that is not that trivial to push certificates to in an enterprise environment. This lead to companies to just discontinue any support for Firefox, why waste time on complex scripts or 3rd party products to manage at free browser, when both IE and Chrome just works?
A lot of users was not happy about this, old habits are hard to change, and browsers are one of the hardest it seems based on all the complaints I saw..
But finally, Mozilla has made some recent changes that will finally enable enterprises to support Firefox in environments with SSL-decryption! Let’s see how it works:
Lets start with my current decrypt policy:
- Rule based on data from MineMeld that updates my PA-200 with IP’s that Office365 runs on.
- Can’t decrypt my XboxOne traffic.. what if I disconnect in a FIFA 17 game? Would be devastating!
- My own list of IP’s based on applications that won’t work with SSL-decryption
- Catch all rule on port 443, even my online bank is being decrypted. You can never be to safe! 🙂
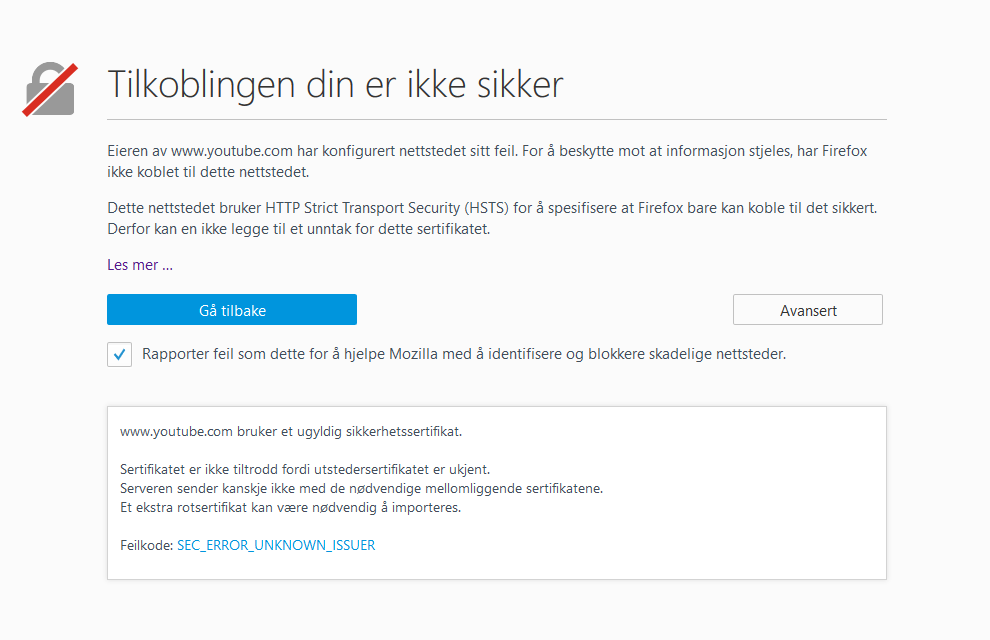
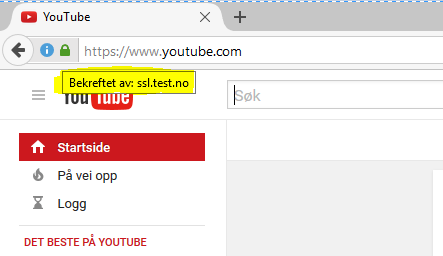
This policy works without any issues on Chrome and IE, since I have imported the “ssl.test.no” certificate into my Trusted Root Certificate Store. But let’s see what happens when I put Firefox to the test?:
Yeah, just as expected. Firefox have no knowledge of the imported certificate, so it stops me from even getting to the site, since it’s clearly a man-in-the-middle(MitM) attack!
The next step in the old days would to import the certificate manually, or get some 3rd party product installed in your domain to do it via GPO..
But now in version 49 and upwards, we have a new cool feature!
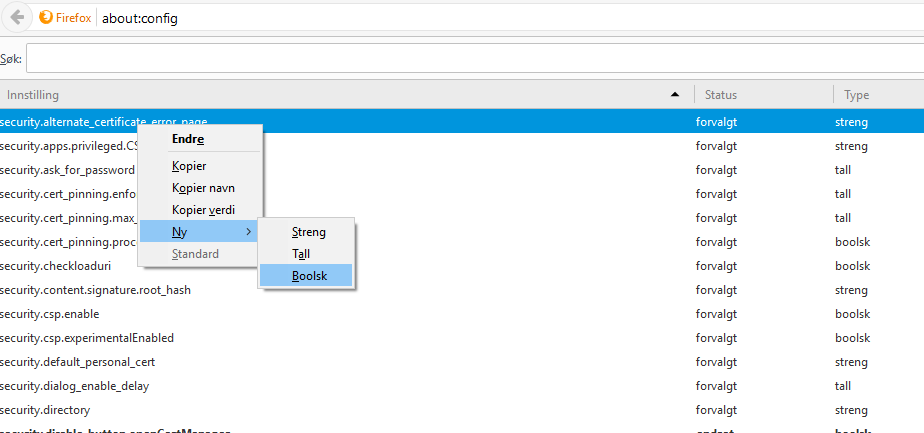
Browse to about:config in the search bar:
Right click anywhere in the list, and choose “New -> Boolean”
Enter the following text into the popup:
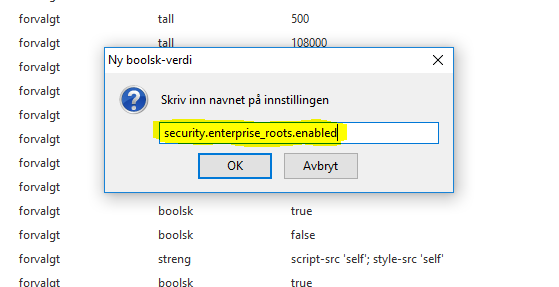
security.enterprise_roots.enabled
Then set it to “true”, and it should look like this:
This setting will make Firefox actually go and check the Windows\Mac OSX certificate store for any Root certificates that it does not have. So basically, it will work like IE and Chrome does!
Restart Firefox, and then browse to a https:// site to see if it works!
And behold, it worked like a charm. I did not have to import anything into Firefox, so it just works! The only downside is that you are not able to see any of the imported certificates in Firefox. This is something that will be added down the line.
But this is one BIG step in the right direction to get Firefox easier to work in environments where SSL-decryption is active. Just remember this is for version 49 and newer!
If you want more information about how to tune Firefox for your enterprise look here:
https://developer.mozilla.org/en-US/Firefox/Enterprise_deployment

The online financial Robot is your key to success.
Link – https://tinyurl.com/y7t5j7yc
Вы реально ? www legalrc com как всё это понять ?
http://intersalat.ru
Thousands of bucks are guaranteed if you use this robot.
Link – https://tinyurl.com/y7t5j7yc
Hmm, it seems like your own site ate my very first comment (it
was really long) so I speculate I’ll just sum that upp thee things myy partner and i had
written and state, I’m thoroughky enjoying your own blog.
I aas effectively is an aspiring bblog site writer, but I’m nevertheless new
to the entire thing. Do you possess any advice
for newbie blog authors? I’d appreciate it.
My blog; situs judi sabung ayam
Trust the financial Bot to become rich.
Link – https://tinyurl.com/y7t5j7yc
Online job can be really effective if you use this Robot.
Link – https://tinyurl.com/y7t5j7yc
Still not a millionaire? Fix it now!
Link – https://tinyurl.com/y7t5j7yc
Financial robot is your success formula is found. Learn more about it.
Link – – https://tinyurl.com/y7t5j7yc
No worries if you are fired. Work online.
Link – https://plbtc.page.link/zXbp
A new company in which over half a year more than 9 million people https://crowd1.com/signup/tatyanaflorida have registered. Profit comes from the shares of the world’s largest gaming channels. Gambling, mobile share with us 50%. Passive and active income. Viber/WhatsApp +12487304178 Skype tatyana.kondratyeva2
Guys just made a web-page for me, look at the link:
https://www.google.com/url?sa=t&url=http%3A%2F%2Fmpxxi.ru/stolovye-nabory-iz-serebra/ Tell me your credentials. Thanks.
Robot never sleeps. It makes money for you 24/7.
Link – https://tinyurl.com/y7t5j7yc
Plants vs. Zombies Cherry Bomb 7 Inch Plush Toy
Manhattan Toy Company 218430 Llama Themed Baby’s First Activity Soft Fabric Book
Р±РѕРЅСѓСЃС‹ casino x
приложение казино х
Guys just made a web-page for me, look at the link:
https://planland-74.webself.net/ Tell me your credentials. THX!
Start making thousands of dollars every week.
Link – https://tinyurl.com/y7t5j7yc
I’m amazed, I have to admit. Seldom do I come across a blog that’s
equally educative and entertaining, and without a doubt, you’ve
hit the nail on the head. The issue is something too few people are speaking intelligently about.
I am very happy that I stumbled across this during my search for something concerning this.
buy viagra online paypal will half a viagra work viagra alcohol side effects
подготовка к егэ с нуля – подготовка к огэ по обществознанию, курсы максимум егэ
казино рокс скачать бесплатно
рокс казино выигрышные
Rhythm Band 6-Note Musical Instruments, Set of 6
Huggies Little Snugglers Diapers, Jumbo Pack, Size 5, 20 Count
In the most suitable way Webshop for Iphone, Samsung and Xuaw
ei Patient
https://www.sms.hr
Buy everything you want earning money online.
Link – https://tinyurl.com/y7t5j7yc
Guys just made a web-site for me, look at the link:
https://videoslotscasino.10ki.ua/a5721-play-bonuses-vs-cash-bonuses Tell me your recommendations. Thanks.
Howdy! lasix fast delivery cost of lasix for dogs
Need money? Get it here easily! Just press this to launch the robot.
Link – https://tinyurl.com/y7t5j7yc
яндекс директ промокод 3000 – купоны яндекс директ втб, купоны яндекс директ плати ру
sauna-v-ufe.ru
use this link гидра
учреждения лечение наркомании – наркологический реабилитационный центр, спайсовая зависимость
Buy everything you want earning money online.
Link – – https://tinyurl.com/y7t5j7yc
Check out the new financial tool, which can make you rich.
Link – https://tinyurl.com/y7t5j7yc
казино фараон играть онлайн в игровые автоматы
интернет казино фараон
browse around this site Empire Marketplace
see this here empire market tor
A new company in which over half a year more than 9 million people https://crowd1.com/signup/tatyanaflorida have registered. Profit comes from the shares of the world’s largest gaming channels. Gambling, mobile share with us 50%. Passive and active income. Viber/WhatsApp +12487304178 Skype tatyana.kondratyeva2
Looking for additional money? Try out the best financial instrument.
Link – – https://tinyurl.com/y7t5j7yc
Everything is very open with a very clear explanation of the issues.
It was truly informative. Your website is very helpful.
Thank you for sharing!
Препараты качественные,купили на сайте anticancer24.ru
Доставили из Москвы за 3 дня
софосбувир +и даклатасвир аналоги
Earning money in the Internet is easy if you use Robot.
Link – https://tinyurl.com/y7t5j7yc
Установка распределительных коробок защищает провода от случайного повреждения. Материал с сайта electrotorg.ru
Magzhan Kenesbai emerging markets expertise
Magzhan Kenesbai energy markets
Make dollars just sitting home.
Link – – https://tinyurl.com/y7t5j7yc
кодирование от алкоголизма цены – наркологический реабилитационный центр, центр реабилитации лечение алкоголизма
Resources empire market alternative links
щедрый вебсайт
Короткие интим истории про жену
Using this Robot is the best way to make you rich.
Link – – https://tinyurl.com/y7t5j7yc
райский вебсайт
https://sexreliz.net/fantasy/1690-fotosessija-ne-sostojalas.html
Make dollars just sitting home.
Link – https://tinyurl.com/y7t5j7yc
Join the society of successful people who make money here.
Link – https://tinyurl.com/y7t5j7yc
+ за пост
_________________
azino777 вход
recommended you read https://hydramirror2020.com
репетиторы по математике спб – курсы подготовки к егэ в спб, подготовка к егэ с нуля
казино франк 100 бесплатных вращений
казино франк на рубли
description bitcoin
Newborn Baby Infant Cotton Pillow Memory Shape Foam Prevent Flat Head Anti Roll Cute Bear Style (Pink)
Sealy Multi-Use Liner Pads with Waterproof Liner, 2 Pack
превосходный веб ресурс
Крутые ххх рассказы про лесбиянок
хорошенький веб сайт
Архив секс историй для взрослых
франк казино вип
франк казино бонусы
Препараты качественные,купили на сайте anticancer24.ru
Доставили из Москвы за 3 дня
софосбувир +и даклатасвир цена +в уфе
Все для лестниц, погонаж оптом! http://35stupenek.ru/ – Комплектующие для лестниц, двери межкомнатные, перила для лестниц, мебельные щиты, балясины для лестниц, деревянные плинтуса, погонажные изделия, имитация бруса, резные деревянные картины, ступени для лестниц. Поможем с доставкой в любой регион!
Препараты качественные,купили на сайте anticancer24.ru
Доставили из Москвы за 3 дня
софосбувир +и даклатасвир +в барнауле
На сайте http://viagraorderuk.com можно заказать и купить для потенции Виагру, Левитру, Сиалис не только по Киеву, а и по всей Украине. Есть препарат Poxet (Дапоксетин) для продление полового акта. Мужские и женские возбудители для горячего секса. Силденафил. Тадалафил. Варденафил. Анонимная доставка Новой почтой
Комбинированные балясины для лестниц! http://td-ekolestnica.ru/ – Комбинированные балясины из дерева и металла от производителя. Мебельный щит оптом, резные балясины, перила для лестниц – поможем с доставкой в любой регион!
Total no risk http://toglobax.com/en/id543485529 You can participate and receive money without any investments. Money does not linger and does not accumulate in the system. No need to order a withdrawal, they are distributed immediately. Instantly. You get money for your own details the very second as soon as paid members appear on your network
1000 продаж за месяц на Etsy через Pinterest https://youtu.be/qg-3C_7W1kM после ужасающего падения количества посетителей в месяц
Комбинированные балясины для лестниц! http://td-ekolestnica.ru/ – Комбинированные балясины из дерева и металла от производителя. Мебельный щит оптом, резные балясины, перила для лестниц – поможем с доставкой в любой регион!
A new company in which over half a year more than 12 million people https://crowd1.com/signup/tatyanaflorida have registered. Profit comes from the shares of the world’s largest gaming channels. Gambling, mobile share with us 50%. Passive and active income. Viber/WhatsApp +12487304178 Skype tatyana.kondratyeva2
The Norwegian Miracle It’s NOT LAMININE anymore! AminoBoosters are 4 times more affordable, the concentration is twice as strong as Laminine by LPGN http://www.getyourboomback.com/#_l_2ps Норвежский ламинин от д-ра Dr. Bjodne Eskeland в 4 раза дешевле американского Laminine и в 2 раза сильнее
Online Casino USA 2020 https://slot-profit.com/ No Deposit Bonuses for US Players 2020. Bonus 20 Free Spins Welcome Bonus 400% up to 4000$. Start with a $20 Free Chip.Welcome Bonus 250% up to 1000$
Элементы лестниц оптом, кухни на заказ, двери из массива дуба – https://www.ekolestnica.ru На сайте большой выбор изделий из дерева (дуб, бук, ясень, береза, сосна): балясины для лестниц, перила для лестниц, ступени для лестниц, двери из массива дуба, мебельный щит! На рынке более 15 лет, отгружаем товар в любые регионы!
ZandCell COVID-19 Saliva Antigen Test https://diamont.ee/en/hot Nitrile gloves, FFP 2 Mask. Large wholesale, from a warehouse in Europe. All documents and certificates are available. Sending samples on request. Contract supplies for government and commercial organizations and individuals
Авиабилеты дешево от проверенных авиакомпаний! https://avia-bilet.online/ – купить авиабилеты недорого. Купить авиабилеты дешево, авиабилеты онлайн. Поиск от 728 проверенных авиакомпаний по всему миру! Самые популярные направления перелетов по самым низким ценам в интернете!