Reducing the attack surface is something I have read, heard and said myself plenty of times.
It’s the strategy I belive in when it comes to security in both business and home networks.
I am also a visual guy that likes to use pictures to show what I mean:
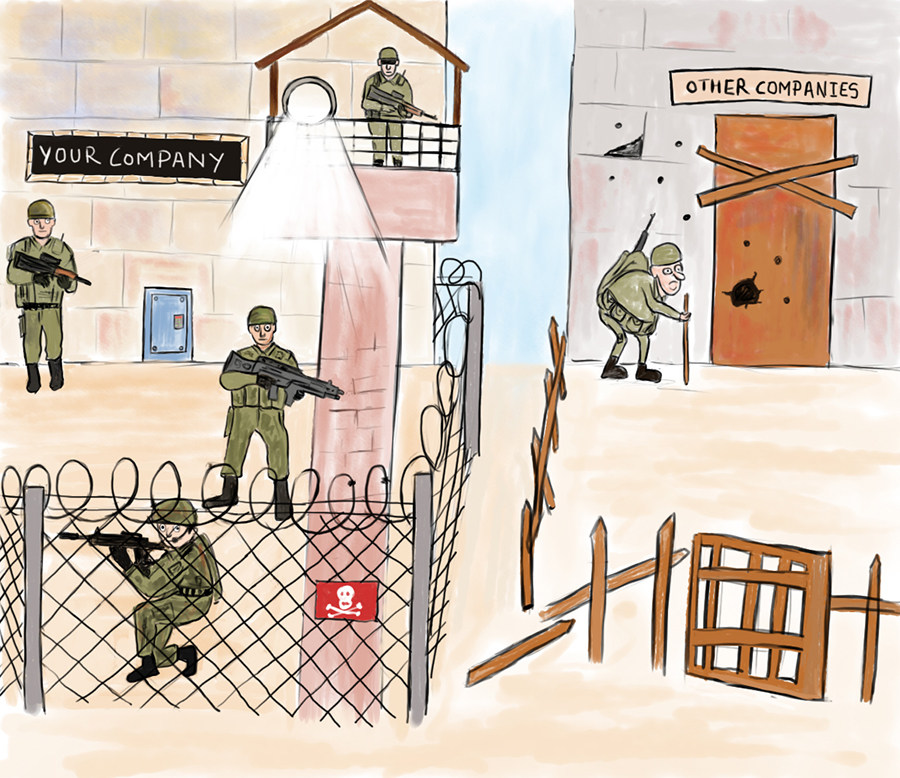
This is a picture I got made from a cartoonist, and its a good representation on how I visualize IT-security looks from an attackers perspective.
Which one do you think an attacker will focus on? They are people just like me and you, they work on the clock and have lives as well. So they will of course go for the one requiring least effort! Why waste time?
This is why I mean that reducing the Attack surface is so important, and the only way to achieve this goal is to have total control on your network! Cause, how can you reduce something you don’t know everything about?
- How many web-serveres do you have? On what ports?
- Do we have any FTP traffic in or out of our network?
- What kind of traffic are we seeing over Port 443? Is it only SSL? If yes, what’s inside that SSL-traffic?
- DNS. Can clients use whatever DNS server they want?
- Web-browsing. Is it controlled in any way? URL-filter?
- Applications. What kind of applications are people using, is everyone work related and safe?
- SaaS. Are people using Dropbox? Google Drive? Outlook 365 private?
- Remote Access. Do people use remote access tools like TeamViewer?
- Internet of Things. What is connected or not? Is the Coffee machine connected? And if yes, what does it do?
This is just some examples you need to know about your network to actually be able to reduce the attack surface. Take control, and find out what is actually happening. And then activate enforcement and control on what you want to go in and out of your network!
You don’t let everyone in to your office!? That’s why we have physical barriers with a receptionist checking who you are before you can get in! Why should you not do the same with your network traffic?
The higher level of control and enforcement you have in your network, the bigger the cost to the attacker to actually be able to breach you! And if the cost is to high, then he will just move over to an easier target.
My point is simple, and can be summarized in one joke:
Do you know how to avoid being eaten by a shark?
Swim faster than the other guy!