Short post. But I have created a small App-ID to identify BankID traffic in your network.
It’s based on identifying the Certificate used in the transaction.
Link: appid_bankid
To install:
Objects -> Applications -> Import = Done!
Short post. But I have created a small App-ID to identify BankID traffic in your network.
It’s based on identifying the Certificate used in the transaction.
Link: appid_bankid
To install:
Objects -> Applications -> Import = Done!
Zone protection is a really important profile to configure on your Palo Alto Networks firewall, since you can stop many network based attacks and reconnaissance of your network.
Many of the settings are just toggle on/off, but the one that give the most value is the Flood Protection tab, and here you need to data from your environment to have any value.
No need to allow 40000 CPS when you never see more than 2000 CPS during peak hours.
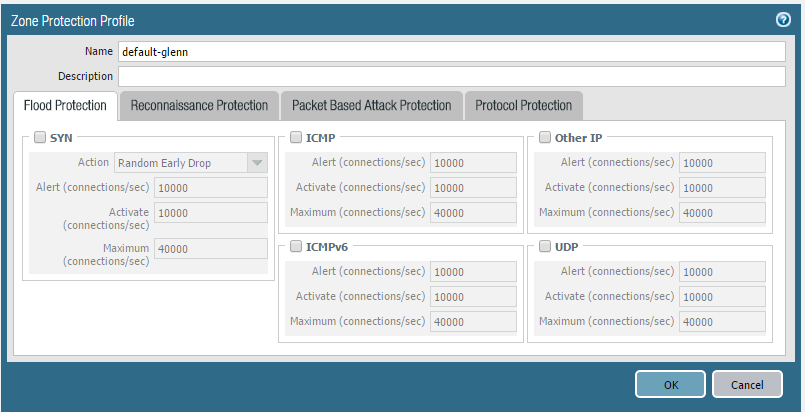
But the problem has been that this information is not that easy to obtain without the right tools, but this have now changed with the release of cpsmine.py!
This is a small python script that can give you a good recommendation on what to fill into the Flood protection tab!
Download the script: cpsmine-py
MD5-hash: 0F290DD81231FFB4CE897956810EABD6
As the extension indicates, this is a python script, and thus you need to install python to be able to run it.
Windows: https://docs.python.org/2/faq/windows.html
Linux: You guys probably already have it installed. 🙂
The script work by going trough logs that you have exported from the firewall, so there is no need for a connection to the API or Management interface of the firewall in any way.
Step 1 – Gather Logs!
Considerations:
You can export the whole log, and then specify what zone or interface the script should filter on. But to save time, I just filter out the data I need directly on the firwall, so the script don’t have to go trough unnecessary log lines.
My filter is on my internal “Trust-VW” zone, and the reason is that I dont host anything, so there should be no connections originating from my “Untrust-VW” zone.
But if you are hosting something, I suggest starting to analyze CPS on the external zone, since Zone protection will give you the biggest benefit there from outside Flood attacks.
After you are happy with your filter, then export it to CSV:
Download the file to a location where you can reach it with the script.
Step 2 – Running the script!
I installed python on Windows, so I am running the commands directly in CMD.
Here you can see the “–help” trigger, and you have several ways to customize the script.
The LOWCPS and HIGHCPS triggers are used to filter out off-peak CPS and abnormal-high CPS so the calculation get the most accurate data that resemble an ordinary day.
The rest is rather self explanatory.
Now let’s run the script!
python cpsmine.py -f log_blog.csv -z Trust-VW -s no
-f = log-file you exported
-z = Zone you want to know CPS
-s = Suppress output or not
Note that “**” indicates that it’s considered in the calculations.
After about 15 min, I get the following output:
And there you have Alert, Activate and Max recommendations based on the log data, which give you a really nice baseline to work with!
Only thing left to do is to put the data into the Zone protection profile!
Good luck!
Note: You can also run the script on specify protocols as well, if you really want to make a granular Flood protection profile.
Did you know that you can auto-populate the log-forwarding and security profile by just calling it “default”?
I for sure did not know it, and I am paid to know everything there is about PanOS.. so maybe this is new for some of you as well?
So how does it work?
Problem/Issue:
You add a new security policy, and you have to manually select the log forwarding and security profiles, on every rule.
We are all human, so accidents will happen where we forget one or both on a rule.
But there is a way to solve that!
Step 1:
Rename or create a new log forwarding profile, and call it “default”.
Step 2:
Rename or create a new security profile group, add the profiles into the group and call it “default”.
Step 3:
Voila! Every new security rule will now auto-fill in the “default” groups!
Now you don’t need to remember the log forwarding, or security profiles!
For most readers, I guess the log forwarding profile will be the most usable one. Since I can’t see any real reason why that should not be enabled on every rule.
Palo Alto Networks official documentation: https://www.paloaltonetworks.com/documentation/70/pan-os/pan-os/policy/security-profile-group