This is a post I have been planning on doing for a long time, but as usual, life happens! But now I finally had some free time to finish this off!
So today I will show how you get started with the amazing new feature in PanOS 8.0, called Clientless-VPN!
https://www.paloaltonetworks.com/documentation/80/pan-os/newfeaturesguide/globalprotect-features/clientless-vpn
This is something I and a lot of customers have been waiting for. The possibility to reach internal applications via the browser, and not need a full VPN connection is really handy!
But even better if you also could remote control servers and desktops?
We can do that as well, but then we need a 3rd party to help us out! We are going to use Guacamole.
Let’s get started!
Step 1:
Login to PanOS, and locate the “Network” tab.
Choose portals, and “Add” or edit a previous you have already enabled.
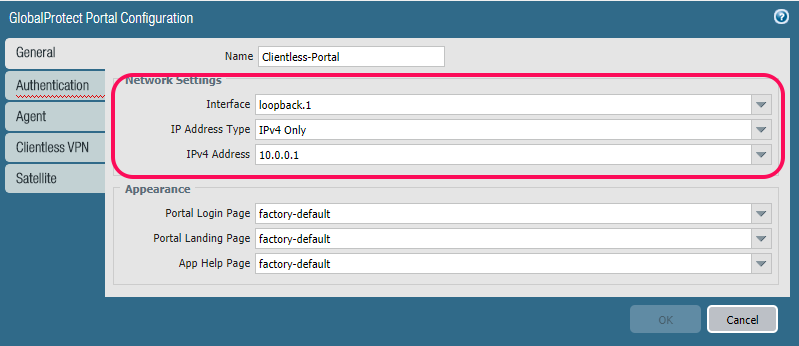
You will then get this configuration screen, and I have highlighted the most important information.
Interface: I am using a loopback interface that is NATed behind my external DHCP address from my ISP. If I had a static external address then I would have used it here. This is the Interface that is needed to be reachable on port https/port 443.
IP Address Type: Choose between Ip4, Ipv6 or both.
IP4 Address: Here you get the choice of IP’s attached to the chosen interface. I just used 10.0.0.1.
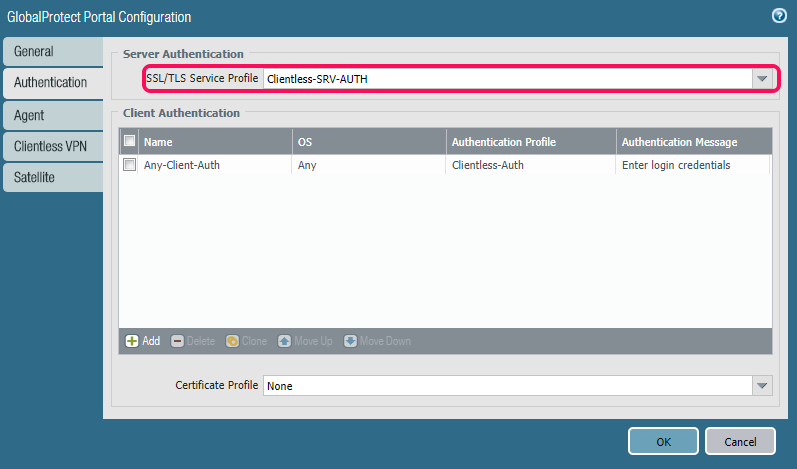
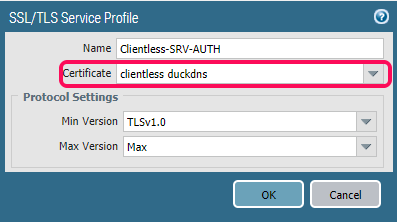
Next is the Authentication tab, and here we need to enable an SSL/TLS Service Profile, and this is simply the certificate we will present the user connecting to the portal.
Let’s create one.
First, choose the Device tab on the top menu.
Then SSL/TLS Service Profile, and choose “Add”.
Here you simply define a name, and add a certificate of your choice. If you don’t have any certificates generated or imported, you can do it directly from this menu.
You can also choose the Min and Max version of SSL/TLS that can communicate with the firewall. I just leave the standard, since that does not include SSLv3 by default.
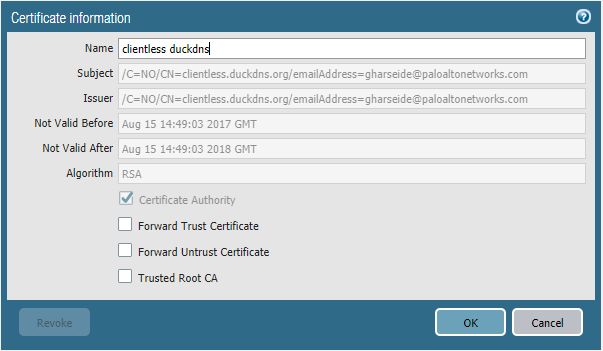
This is the certificate I am using, I generated it directly on the firewall.
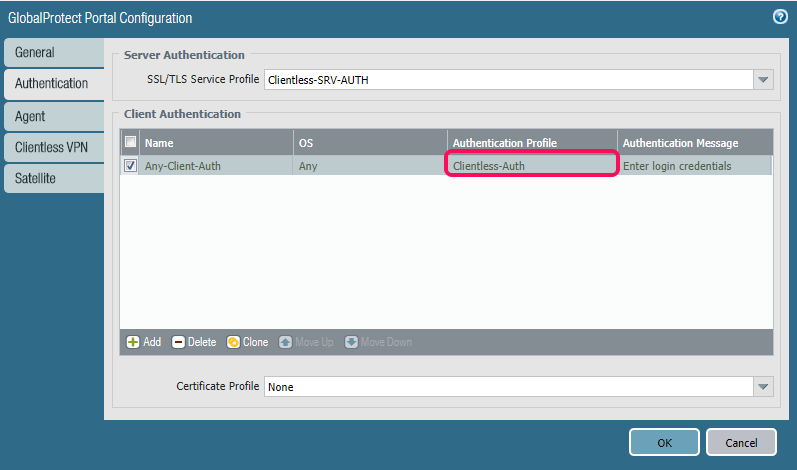
Now that we have an SSL/TLS Service Profile in place, the next step is then to actually define who can log in and access our portal.
Just push “Add” in the Client Authentication frame to add a new rule. We have the possibility to tune the rules for individual operating systems as well.
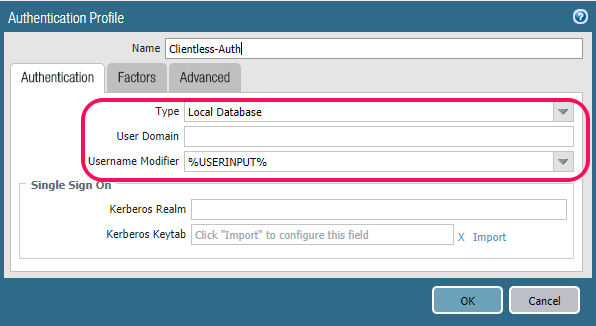
But the most important part here is the Authentication Profile, which is outlined.
Let’s create one of those as well if you don’t already have one.
Back to the “Device” tab on the top menu.
Select Authentication Profile, and push “Add”.
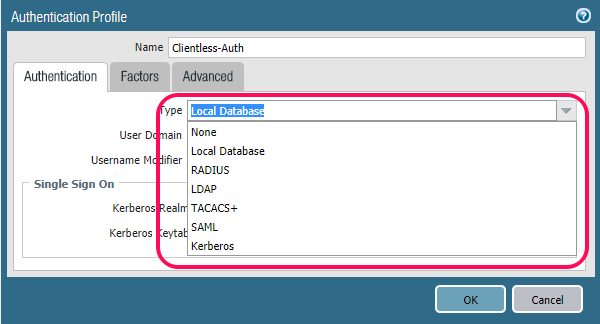
Here you can configure the Authentication profile, I am just using the Local Database on the PA-220, but here you can choose between several types of user catalogs. You can also add 2-factor via the “Factors” tab as well. Look at my previous post to see how that works!
As you can see, we have many ways to authenticate users. Local as said is the simplest one to get started.
When you have configured the Authentication part of the portal, then we jump down to the “Clientless VPN” tab, and everything here is new in PanOS 8.0.
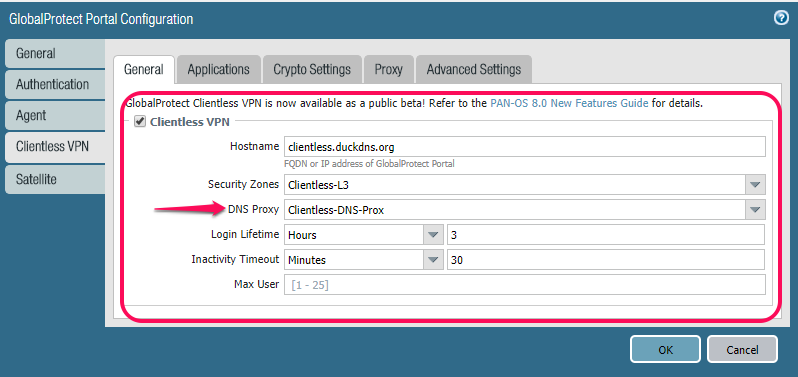
First, you need to check the “Clientless VPN” frame, to enable the settings.
Hostname: I use a dynamic DNS provider called DuckDNS, so I entered the full hostname here for the portal. IP will also work just fine.
Security Zones: This one is important. Cause all traffic coming from the Clientless VPN will originate from this Zone. So if you create a Zone just for this, then you need to make sure you have a security policy that gives access to the features you want.
DNS Proxy: We need to have a DNS Proxy in place on the firewall, so the firewall is able to process and redirect traffic as needed via the Clientless VPN.
The rest of the settings are self-explanatory. Let’s create a DNS Proxy!

Make sure you are on the “Network” tab on the top menu.
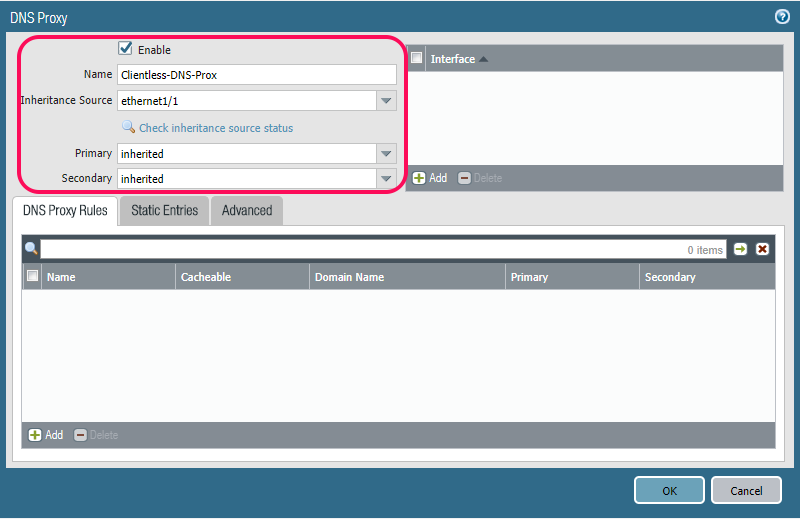
Choose DNS Proxy and press “Add”.
Make sure you check off Enable and give it a name. Next is to either choose an interface to inheritance the DNS servers from or enter them yourself directly into the Primary and Secondary fields.
The rest is not needed at the moment, but you can make DNS Proxy rules on how to forward DNS traffic. As an example, you can forward all DNS request for your domain to the internal DNS server, and the rest is forwarded to external DNS servers like googles.
Add it to the configuration and jump to the next part.
Since we still are under the “Network” tab, just jump to the Clientless Apps section, and press “Add”.
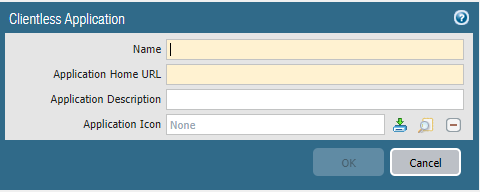
We will then get this simple configuration pane.
Name: What the application will be named when logged into Clientless VPN
Application Home URL: FQDN or IP will work here. But remember to put HTTP or HTTPS in front. This will help as redirects are not always working perfectly.
Application Description: A simple description of what the app does, will show when you hover the mouse over the Icon on Clientless VPN.
Application Icon: You can upload customized icons if you want.
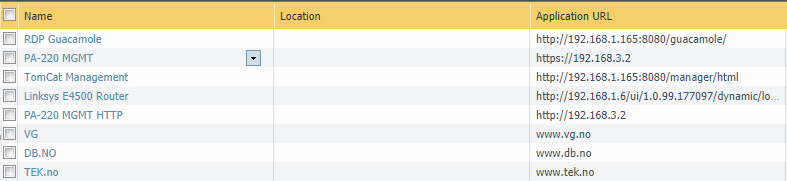
This is the apps I currently have live on my PA-220. Out of those, it’s the one on the top that is used the most.
Next is to add them to the Clientless VPN configuration.
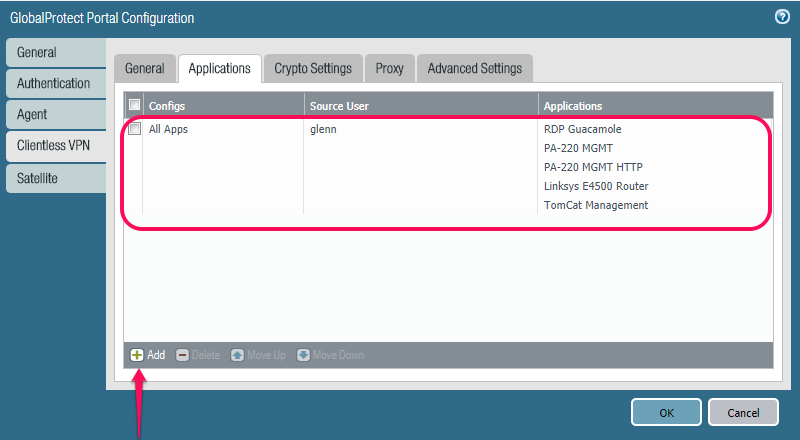
Back to the Portal->Clientless VPN configuration, but now we jump to the “Applications” tab.
Here you just add apps via “Add”, and you can give different users/groups different apps.
So if this was in production in a large company, maybe IT-admins would get one set of apps, while HR another etc etc..
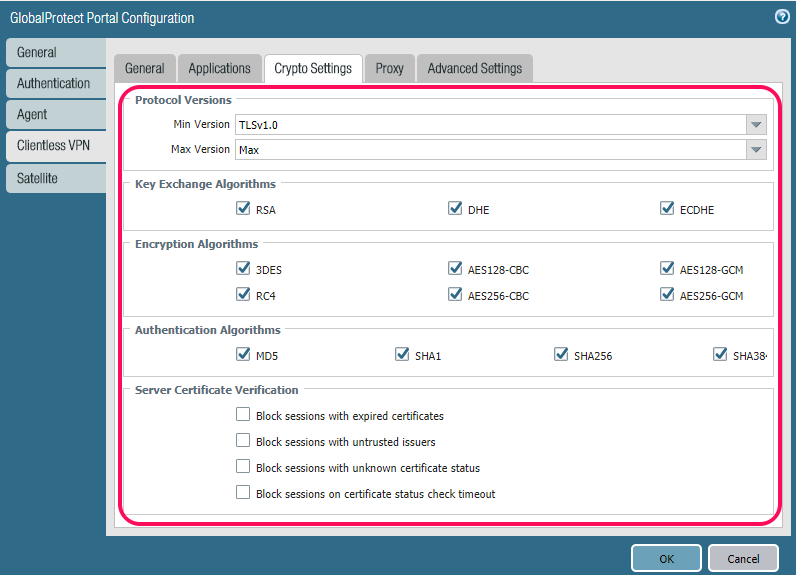
Next is the “Crypto Settings” tab, and this is just rules on what kind of protocols the PA-220 is allowed to use to communicate with the Clientless Applications you have defined.
So if you have an application that doesn’t support any of these, then PanOS will not be able to establish a connection. Here you can depreciate down to SSLv3 if you want.
We now have a working portal with Clientless VPN!
Step 2:
Clientless VPN is up and running, but we need Guacamole as well to be able to use Clientless VPN as a Remote Desktop tool!
http://guacamole.incubator.apache.org/
This is the tool, and it works amazing!
I am running it on a Raspberry Pi3 with raspbian without any issues or performance problems at all.
There are several installation scripts for it, and I have tried 2 of them (I am lazy when it comes to Linux):
http://chari.titanium.ee/script-to-install-guacamole/
And
https://sourceforge.net/projects/guacamoleinstallscript/
Created for CentOS.
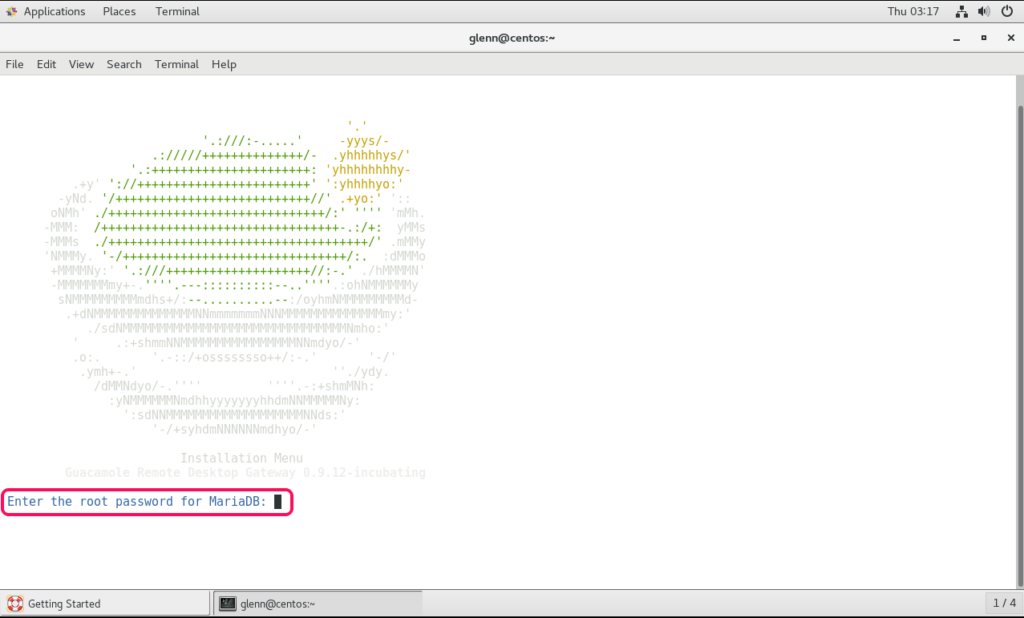
This is how it worked on my demo-install:
I ran the script with “sudo root <script.sh>” and it gives you steps to follow. It will take around 10-20 min.
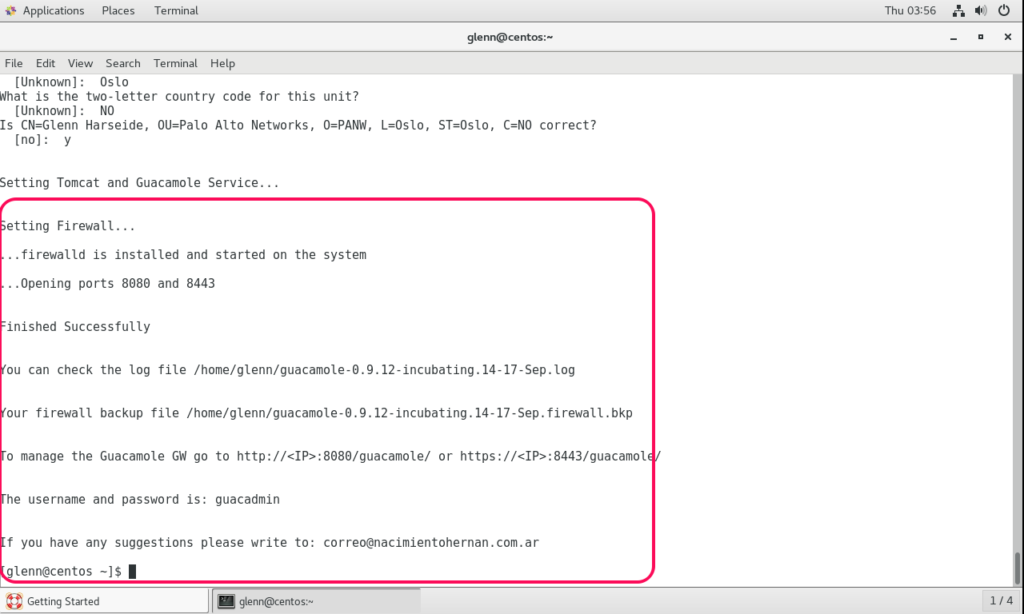
It will install Guacamole and all needed dependencies like TomCat, Java etc.
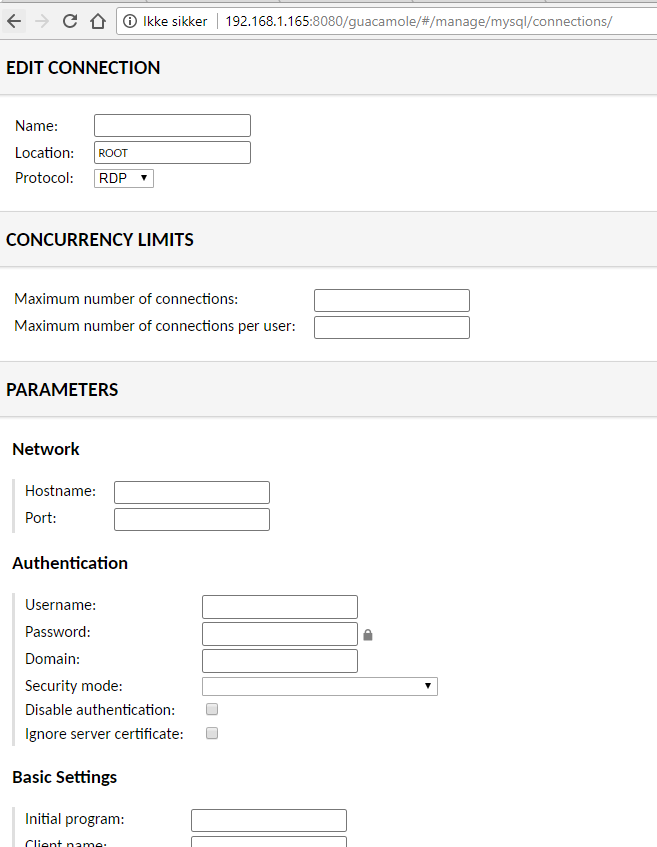
Done! Now the only thing you need is to log in and add the RDP connections you need.
Guacamole supports RDP, VNC, Telnet, and SSH.
When you have added some connections, then it’s time to test it out!
Step 3:
Log in!
The login screen is the same as before to get the GlobalProtect-client from the firewall.
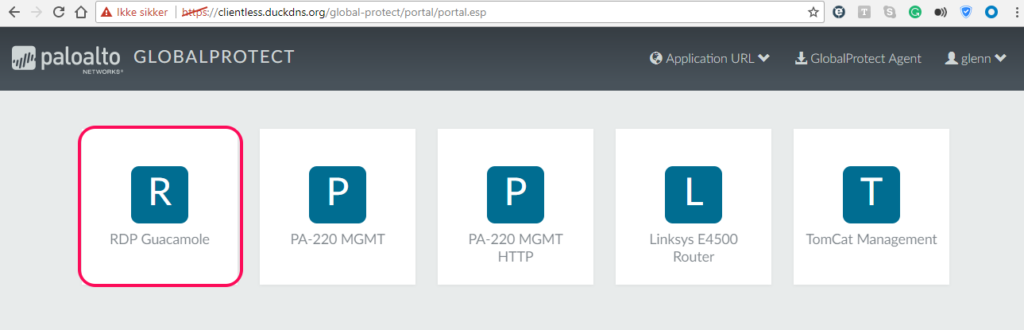
Use a username and password that will authenticate, and you will get to this screen:
Notice in the right corner, that we are able to enter an Application URL directly as well, and that we also can retrieve the GlobalProtect Agent as well if needed.
I choose the “RDP Guacamole” application.
And it sends me to the internal login of Guacamole.
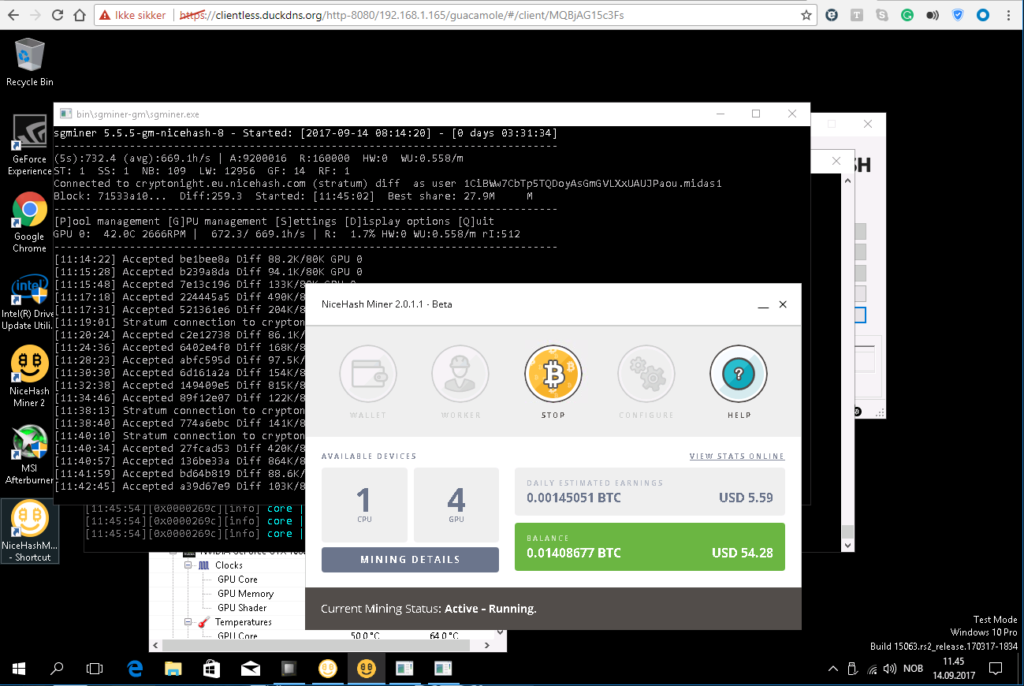
This is the URL String using Clientless VPN: https://clientless.duckdns.org/http-8080/192.168.1.165/guacamole/#/
Lets login.
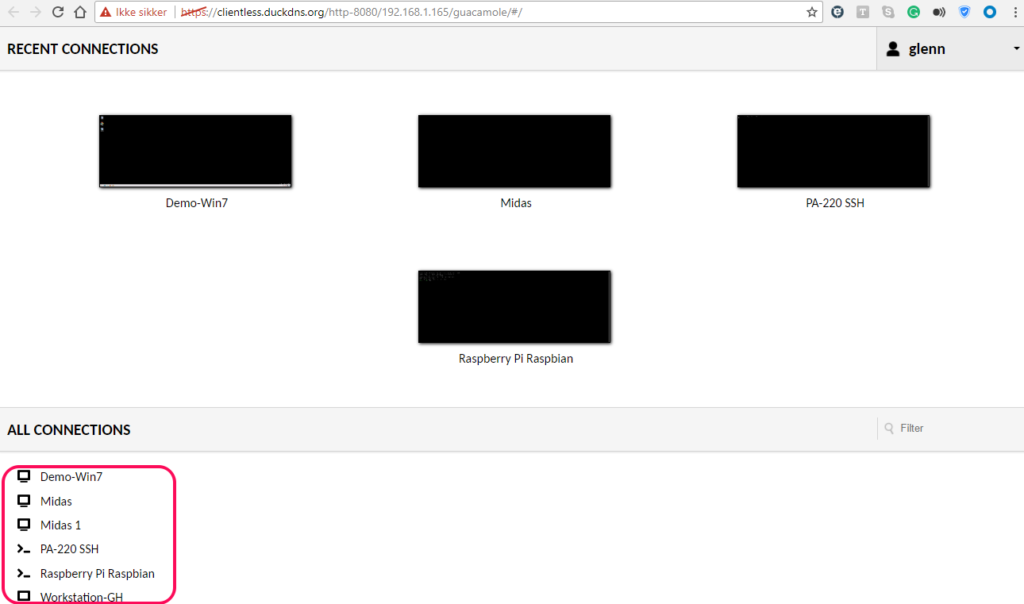
I am greeted by my Recent connections on the top, and the list with all available connections.
As you can see, I have 4 RDP and 2 SSH connections.
It’s really nice to have SSH access to both the Raspberry Pi and PA-220. Makes it much easier to work and test anything from anywhere.
Midas and Midas1 are my cryptocurrency miners, and it’s nice to be able to maintain them from any device. I have more than once logged into them from my phone to verify that everything is running smoothly.
Let’s see how it looks.
There you have it, a full desktop experience via the browser. It behaves just like a regular RDP session would.
Have fun!



If some one wants to be updated with hottest technologies after that he must
be visit this web page and be up to date all the time. https://anunturi-parbrize.ro/parbriz-rolls_royce-58.html
A fascinating discussion is worth comment. There’s no doubt that that you ought to write
more about this subject matter, it might not be a taboo subject but typically
people don’t speak about such topics. To the next!
All the best!!